Would you believe a 15-year-old hacker stole $23 million using the SIM swap fraud?
Well, by the end of this article you’ll be amazed at an intricate world of young hackers wreaking havoc globally and locally.
The article is twofold.
The first part (PART A) explains in detail how and why the SIM Swap fraud occurs in the US under telecom carriers like AT&T, Verizon, and T-Mobile.
The second part (PART B) uses these insights to explain how SIM swap is done in the context of Kenya under the Safaricom Telecom Network.
You’ll better understand how Kenyan hackers are engaging in M-pesa-based financial fraud by first understanding the origins of the scam and the real inspiration.
Some general information first.
Why do Hackers Perform a SIM Swap?
There are different categories or avenues for SIM swapping. These are also the reasons why people get chosen as victims.
To Steal High-value Social Media Usernames
First, people with high-value social media usernames can be targets.
Social media usernames can be sold for thousands of dollars and so hackers social engineer victims in order to gain access to their accounts.
In this case, a SIM swap is done to help hackers get the authentication codes needed to change logins to your social media account.
Once they are in your Instagram account, for instance, they change your username to something different. They will then create a new account – on a separate device and with different details – but with the username that used to be yours.
In such a case, even if you report your account as hacked, Instagram will block the account but the username will already be under a new account and cannot be returned to you even if you get your account back.
To Withdraw Money from Hacked Online Bank Accounts and Mobile Apps
The second reason is bank fraud both online and on mobile apps.
The US has a lot of financial fraud across different domains but predominantly there is online banking fraud.
Once hackers take over your online banking email and password, they will SIM swap your number in order to get the two-factor authentication code (2FA) that will allow them to transfer the money.
This kind of swapping is less common since hacking bank accounts needs real knowledge of money laundering; which only a few people may understand.
Money laundering is meant to make the transactions untraceable.
To Steal Money from Cryptocurrency Wallets
The third reason, and one that this article dives into in-depth, is the cryptocurrency-based SIM swap.
Currently, SIM Swap fraud in the US is catalyzed by the fact that a vast majority of users on major Cryptocurrency exchanges such as Coinbase use text-based (getting a text to your phone number with a login code) two-factor authentication (2FA) to login.
Let’s now look at SIM swapping in the context of the US.
———–
PART A – THE US
How the SIM Swap Target (Victim) is Chosen
Choosing a target is easy yet goes through complicated steps.

The first step in hacking a cryptocurrency wallet is finding the victims in the first place.
How Hackers use Combo Lists and Leaked Databases to Find Targets
A COMBO LIST or simply leaked databases are used to identify potential accounts to target.
A leaked database will contain email addresses and dehashed (cracked) passwords.
These databases are often gotten from hacked websites.
You may have heard of data breaches at big companies for example when Marriott International had 500 million customer records stolen. Other leaks include Yahoo, Adobe, Ledger, LinkedIn, etc.
The leaked data contains different bits of information but most importantly it has emails and passwords. Hackers will cross-check these details over multiple websites to try and identify users who repeat passwords on different service platforms like Netflix, Hulu, etc.
These stolen customer details from data breaches are posted on sites like raidforums.com and cracked.to and can be obtained by anyone at a small fee.
Now, often, such databases will have names, phone numbers, emails, and passwords. The passwords are however hashed (meaning they are not displayable in plain characters).
Dehashing Passwords from Combo lists and Other Databases
Therefore, the next step for a hacker – or chain of hackers – is to de-hash the passwords.
You might think it is impossible to crack (dehash) one password and you’d be correct. However, when you have a list of 500 million passwords, you can find weak hashes – via automatic password cracking tools – that can then lead to easy decoding of the rest of the passwords.
Also, a hacker can simply cross-reference one database leak with a different one to see if a user (going by the email address) has reused their password in different websites. E.g., is there a user email and password that works on both Adobe and Netflix?
This is how you find people on the darknet selling Usernames and Passwords to sites like Netflix, HBO, Papa Jones, Chipotle, etc.
“Free” Food from Hacked Food Ordering Apps
Since apps from food companies like Papa Jones are often connected to a credit card, the hacker can then just download the app, use the stolen logins and order food at the expense of the real account owner.
There are actual dark web chatrooms where people order food for cheap by simply contacting hackers and stating what they want and paying a tiny fee.
The hacker then places the order via the stolen account and the food is delivered to the requested address. The real account owner suffers because they might get charged a lot of money before they can effectively block the account or delink their card.
There is a whole marketplace for these logins – called LOGS in the dark web – as some hackers are dedicated to finding as many logs to as many services e.g., Netflix, HBO, HULU, and food delivery companies with apps.
Full-access and non-full-access Hacked LOGs
LOGs can be full-access or partial access.
Full-access LOGs contain logins to the victims’ email addresses and also other services like their Netflix account.
When a hacker gets a victim’s email address and password, they use tools such as the Yahoo Ranger to scan the email contents of specific keywords like ‘Netflix’, ‘Apple’, ‘HBO’, ‘AMX’, ‘Chipotle’, ‘Bank of America’, etc.
Notably, a hacker can also just get a COMBO list (email and de-hashed passwords) and use tools like Sentry MBA, Openbullet, or Silverbullet to try if the login combination works on any major sites.
A tool like Sentry MBA will automatically do 5,000 login attempts per second.
They then sell the working logins at about 3 cents per account. They can sell over 10,000 of these per day hence making about $3,500 each day.
With the above background, you now understand how databases are found and how hackers get login information.
The Ledger Database Breach and Crypto Fraud
In Crypto, one of the most important databases was the Ledger database breach in 2020.
Ledger is a company that offered its users physical cold wallets for their coins.
Obviously, someone using a Ledger wallet has a significant amount of cryptocurrency in their wallet.
The Ledger data breach contained users’ names, email, physical addresses, and phone numbers. It did not have passwords or crypto keys.
However, hackers used cross-referencing to determine the right targets.
The Ledger email would be cross-referenced with other leaked databases to see if it matches with other emails in any other databases and from there see if it is associated with any passwords.
Then, the hacker would try the email – passwords combos on crypto exchanges like Coinbase to see if they would work.
The motive of this trial-and-error method with logins (email and password) is to find the current exchange associated with a user.
First, knowing a person’s logins for a specific crypto exchange is very valuable information.
In addition, just knowing if a person is registered to a specific wallet is by itself critical information.
Crypto exchanges know this and they instituted measures to curb these attempts.
For example, if you type an email and a password, your login is simply rejected and you will not know if the person is registered with that exchange.
However, hackers use the email to try and register for a new account and this automatically notifies them if an account already exists with the email in question.
The second safeguard by crypto exchanges is the requirement to have a two-factor authentication (2FA code) or a third-party login authenticator like Google authenticator to log in.
How Hackers Know the Amount money a Person has in their Crypto Wallet
Before targeting a victim, hackers often try to establish if the victim has enough money in their Crypto wallet to warrant an attack; these attacks are expensive and require multiple people so they cannot be wasted on a wallet with a low balance.
It is alleged that Coinbase had a bug (exploit) that allowed anyone with a valid password and username to check account balances. It did not need a 2FA code or any other authenticators. The bug was only present for a month.
Over 6,000 users were affected by this bug (https://www.reuters.com/business/finance/coinbase-says-hackers-stole-cryptocurrency-least-6000-customers-2021-10-01/)
Hackers would just run millions of username and password combinations until they found the millionaires of Coinbase.
The vulnerability in Coinbase also allowed hackers to see whether an account needed a text-based 2FA or an alternative such as Google Authenticator.
Accounts using text-based authentication were the primary targets.
How do Hackers Find Out Target’s Phone Numbers?
Well, on the login page of Coinbase, a user is asked to enter the code sent to the phone number with the last few digits being displayed e.g., “Enter the 7-digit code we sent to XXX XX 54”.
The hackers would do phone number tracing or ISP doxing using these last two digits. The resulting endpoint gives the real name of the individual and the last two digits of their phone number.
They then do a White Page search on the person.
This reveals their full name, physical location, full phone number, etc. Also, by the fact that the person’s email and password (to Coinbase for instance) were leaked online, there is a chance that their number is on those stolen databases too.
The next step is to match the number to a phone carrier e.g., Verizon or AT&T so that the right procedure is used in the SIM swap.
Up until this point, you’d probably think this is too much work.
However, selling the information of the right SIM swap target is a market of its own on the darknet. It is a chain of events involving different people.
The actual hacker swapping the SIM could just step in right here and take over the process.
How the actual SIM Swap is Done
The first step is a RECON (short for reconnaissance) of the mobile carrier’s store.
The hackers need the tablet used by the store manager and their password in order to successfully swap a SIM. So, the recon is to help plan the robbery.
The robbery process is called a REMO (remote tablet grab). A thief is paid by the hackers to run into a store and snatch the tablet.
Before the REMO, the RECON helps with social engineering the store manager. An example is placing a call to the manager pretending to be at the carrier’s headquarters and requesting them to log in to a link (that you send them in the moment) to solve a customer ticket.
The link is a fake URL and is meant to capture the manager’s password and other details. The link is made to look like the legitimate carrier’s internal web dashboard.
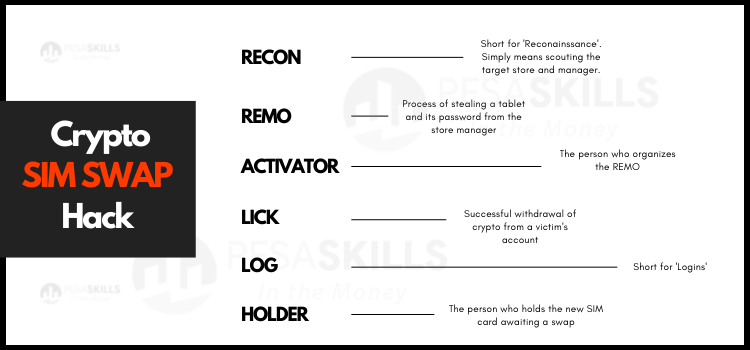
(Carriers such as T-Mobile have been said to issue memos to curb this fraud by ensuring that store managers report such theft immediately. Often, the tablet is disabled within 10 minutes).
The tablet thief is the lowest paid in the chain – earning just around $200.
The thief then hands over the tablet to a person waiting nearby who is usually skilled in operating the specific carrier’s software system. They could be a former employee at the store or just an individual who has been taught how to work the system.
Now, the guy with the tablet is not the same person who is stealing money from Coinbase. Remember, we said this is a chain of people.
The actual Coinbase hackers are alleged to operate from Telegram Groups – Chatrooms.
A group will come together and organize for a REMO and be ready for the SIM Swaps.
They often pay the person doing a REMO up to $10,000 per number that is successfully swapped.
A T-Mobile swap costs $5,000 or $7,500 if the number is tied to a fraud victim. Fraud victims have special protections against swaps.
A Verizon swap costs upwards of $50,000. They are well secured but still possible to work. For Verizon instead of a store manager login, you need a branch manager’s login. For this they need an insider; a hacker is not possible.
An AT&T swap costs $2,000 to $4,000.
The hackers in the chatroom simply wait for an active REMO to be done and they provide the specific numbers they need to be swapped.
The surprising fact is that these hackers are sometimes teenagers. Also, the process between a REMO and the swapping is so intense because it happens in a very short span of time. (Remember the stolen tablet gets deactivated in about 10 minutes).
In those 10 minutes, a lot needs to happen for a successful swap and hence con.
Telegram Chatroom members are notified hours before a REMO is done.
An ACTIVATOR coordinates the REMO.
The Activator will let everyone in the Discord channel know that they have done the REMO and immediately they receive swap requests from Telegram.
The hackers send the activator a phone number and the ICCD.
The ICCID Number stands for Integrated Circuit Card ID. It is a 19- or 20-digit number that’s typically printed on the back of a SIM card.
In the 10-minutes window, the activator tries to swap as many numbers for different hackers as possible.
The activator will make over $100,000 from a successful operation.
A successful login is called a LICK. So, a hacker will say they licked someone when they successfully get into their Coinbase account for instance and transferred the funds. A login is simply called a LOG.
Now, because mobile carriers geofence login to device accounts, the hackers use proxies to bypass this part.
Before a REMO, the hacker prepares by setting up the proxy.
They will then use the proxy to login to the victim’s email account and change the password. This will be followed by a Coinbase login since the device authentication link by Coinbase will be received on the email.
The process also involves a HOLDER. The holder is someone that is holding a phone that will get the newly swapped number and to which the OTP link will be sent to by Coinbase.
The hackers do not hold the new phone with the swap because of operational security.
Both the attempted login to the email and to Coinbase require the holder to constantly communicate with the hacker by sending the OTP link or any required code as sent by either Coinbase of the email company.
What Happens After a Successful SIM Swap?
Once inside Coinbase, the hackers move the funds to Coinbase Pro so they can transfer them in bulk to their Meta mask wallets.
Some of the hacked accounts have millions of dollars in them.
Coinbase Pro has a higher daily withdrawal limit. Still, the amount in the wallet could exceed the withdrawal limit for the Pro account. Several workarounds exist for this part including using bots to spam request the account until it allows for such withdrawal.
That way, they can transfer over $250,000 or even $1,000,000.
According to the Darknet Diaries, most of these hackers that are millionaires are younger than 16 years!
Michael Terpin, a cryptocurrency investor and millionaire, lost over $23 million in a similarly executed scheme by a 15-year-old hacker named Baby Al Capone https://nypost.com/2020/05/23/baby-al-capone-ellis-pinsky-pulled-off-a-23-8-million-crypto-heist/
Now onto the case of Kenya.
————
PART B – Kenya.
Kenyan Police Boss lost Kshs. 600,000 ($6,000) in a SIM Swap Fraud
On January 4th, Peter Mwanzo, the OCPD (Officer Commanding Police Division) for Kasarani lost approximately Kshs. 600,000 in a well-coordinated scam.
Testifying in a Nairobi court, Mwanzo narrated how in a span of 6 hours he fell victim to the fraudsters who SIM Swapped his phone number and took out money in lump sums.
The first step of the SIM Swap was getting Mwanzo to switch off his phone.
He recalls getting incessant phone calls from a strange number. He turned his phone into flight mode at 6:45 pm as a result of the disturbance.
When he deactivated the flight mode, at about 6:50 pm his phone did not pick up the Safaricom signal.
The signal was lost all the way to 9 pm when he was leaving his office.
The next day Mwanzo went to a Safaricom store due to the frustration of lacking network access.
He was advised to replace his SIM card and upon reactivation, he was surprised at the number of messages coming in. The hackers had taken out all his M-Pesa balance and even gotten loans from Fuliza and Airtel money both of which he had never registered.
He was surprised that they had his banking information too which he never stored on any device.
His Equity bank account for instance had a withdrawal to M-Pesa of about Kshs. 597,100.
The money was then withdrawn from an M-Pesa in Bomet, Kenya.
Now if you read the story above, you might have a clue how this scam happened.
The Safaricom SIM Swap Fraud
There is a very good theory on how SIM swaps are done in Kenya and it is inspired by the same scam being run in the US.
(Please note this section is based on my opinion and speculation and not factual evidence).
The first phase is that the hackers get you offline. They want you to either switch to flight mode or switch off your mobile phone.
This is because Safaricom cannot allow an active number to be swapped.
And the procedure for a legitimate SIM swap is very easy.
You can either visit an M-Pesa agent with;
- Your old Safaricom number
- Your original Safaricom SIM card PIN
- Your old line should have an active M-Pesa account
- Your original ID card Some cash either Ksh 50 or Ksh 100. It is free of charge to replace a postpaid line.
Or you can do the swap yourself if you have the following:
- A replacement SIM card from your local store. It retails anywhere between Ksh50 and Ksh 100, depending on your location.
- Your old phone number
- Original SIM card PIN
- A previous active M-PESA
For this self-swap procedure, you simply:
Insert the new SIM card into your device and dial*180*1*mobile no.*Original Pin* IMSI#.
For example, if your number is 0720123456 and your PIN is 3434, then it should be like *180*1*0720123456*3434*IMSI#.
Where IMSI is the serial number of the replacement SIM Card.
In both instances of swapping at an M-Pesa agent and the self-swap, you need to have the PIN number of the SIM being swapped.
However, a third option exists where you can call Safaricom customer care with a few of your details including full names, ID number, last top-up amount, current M-PESA balance as well as the recent M-PESA transaction details.
If you provide these details accurately then they will replace your SIM.
At this point, you may be wondering how the swap is done. Well, that’s where social engineering comes into play.
Social Engineering and the Safaricom SIM Swap.
Social engineering is a term that means manipulating or tricking someone to disclose sensitive information such as their SIM PIN.
Initially, the hackers would call a victim’s number pretending to be Safaricom customer care agents and get them to disclose their details including full names, ID number, last top-up amount, current M-PESA balance as well as the recent M-PESA transaction details.
This is an example of social engineering.
To make it believable, hackers would use phone number spoofing software to mimic the official customer care number from Safaricom – 0722000000.
With the obtained details, a hacker can simply call the official Safaricom call center and get your number swapped (as long as they get you to switch off your phone first).
Beyond the victim, social engineering also happens to M-Pesa agents and Store managers.
This is the same approach US hackers use to get information from store managers at mobile carriers’ official locations.
This means that using malicious links, for example, it is possible to obtain passwords to the devices (tablet) a Safaricom store manager uses, and then a thief can be sent to steal it.
Such a tablet can be used to swap SIMs fast and without many details being needed.
However, Safaricom has never reported such an incident meaning it is highly unlikely.
More accurate speculation is that social engineering is being used on M-Pesa agents to get them to swap the numbers.
An M-Pesa agent is authorized to do a swap and because they know the system well, they can manipulate their way through even without some details.
An Insider Job?
Techweez reported that they suspected that the SIM swaps were being done with the help of rogue employees at Safaricom.
This theory would be accurate because the same thing is being done in the US.
In this other article HERE, I go into detail about possible and alleged insider jobs by Safaricom junior staff at the GSM department.
As noted in part A of the article, mobile carriers such as Verizon cannot be easily hacked and so the hackers pay rogue employees handsomely to help perform the job.
That’s why it costs as much as $50,000 to swap a Verizon number.
In the same way, it is possible that some high-level employees at Safaricom are paid well for them to fraudulently swap numbers for hackers.
It could also be possible that some rogue M-Pesa agents are being paid to facilitate the swaps.
How Hacked M-Pesa Numbers are used to Get into Your Bank Apps
When someone has taken over your phone number and has your M-Pesa PIN, they have control over a lot of areas of your life including your banking.
Remember how US hackers used bots to search through hacked email to find which services a victim had subscribed to? Well, think of the same situation here.
A hacker can simply download all the famous banking apps locally and try login into each one and eventually they will find the one that you use.
And because they have your number, any OTP sent by the bank will go to them. This way, they can transfer money from your account without visiting the bank.
Also, with your phone number, it is possible to sign up for loan services from different mobile apps or other telecom networks and take out huge loans on your behalf.
Malicious links, Leaked Databases, and the Safaricom SIM Swap Fraud
A lot of people wonder how hackers find information about them.
In some instances, it is a very easy social engineering process. Just like in the US where hackers use spoofed links to get passwords from store managers (of big telecom firms), the same approach is used locally.
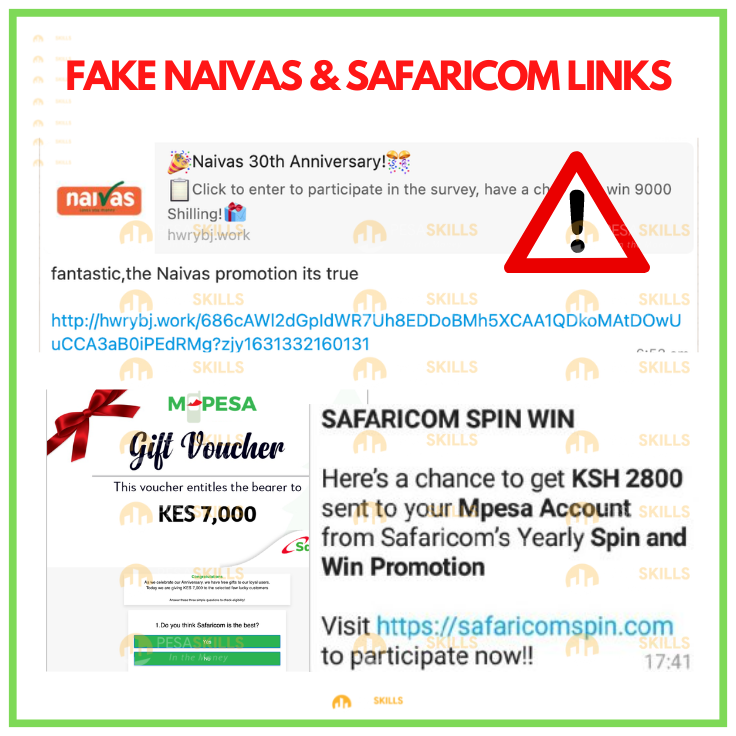
Techweez for instance speculated that some third-party money lending apps in Kenya are collecting information that is somehow later passed on to hackers and used for SIM swap fraud.
This is an accurate theory because these money lending apps have very deep permissions on your phone and can access even your call history, read your messages, see the other apps that you use, etc.
It would not be surprising if some of the unchecked money lending apps log your keystrokes such that they can tell which passwords you use for specific apps.
Now imagine a hacker with a leaked database from a mobile loan app that contains names, locations, contacts, apps used, messages, maybe PIN, and other details of hundreds of thousands of Kenyans.
Also, the fake coupon links being spread on social media are part of the social engineering that lets hackers get people’s login details to different accounts including M-Pesa details.
Here we are talking for example the fake Naivas coupons or the Free Airtime links on WhatsApp.
When you click on the link, you may fill out fake forms that store very important details about you including passwords.
How to Prevent the Safaricom SIM Swap
Here are a few cautionary steps that you can take.
- Do not pick or engage a call from Safaricom “customer care” when the number starts with the +254 prefix. So, if you get a call from 0722000000 it is legitimate but if it is from +254722000000 it is most likely a spoofed (fake) number.
- When you get several calls from a private number for no apparent reason, do not switch off your phone or turn on the flight mode. Just block the number instead.
- If you get a message about a requested SIM Swap, immediately report it to Safaricom’s customer care. The same goes for when you receive messages about transactions that you have not initiated or made.
- Do not give out your personal information – especially your ID number and PIN – to anyone pretending to be a customer care agent.
- Avoid clicking on suspicious links on social media and also avoid downloading mobile apps that are not from the official Google Play or iOS app stores.
Additional steps to protect yourself against a SIM swap, especially in the US include:
- If your account has the option, add extra security of having to verify the 4-8 digit passcode every time you go to a store or call in
- Have customer service leave a PRIORITY NOTE on the account stating “No one besides the account holder is authorized to swap sim cards – account holder must be in-store and verify 4-8 digit passcode”.
- Setup a sim pin in case your phone is ever stolen. Scumbags will put your sim card into another phone and if they have any of your info it is basically game over.
- Create a FREE number with Google Voice. Google Voice is a free call forwarding app that allows you to call and text while not charging you. While my number is actually 1234567890 I have a GV number that is 0987654321 and I give that out to banks/whatever. Google Voice numbers cannot be sim swapped. Even if you are sim swapped, the person doing so will have no access to your Google Voice account.
(Credits to this article go to the Dirty Coms podcast episode from the podcast Darknet Diaries by Jack Rhysider. Listen in here – https://darknetdiaries.com/episode/112/)


















