Isn’t it bizarre how a hacker can simply get control of your phone number in a few minutes?
If you are as curious as I am, you have probably wondered how exactly a SIM swap fraud is done in Kenya. And maybe what Zuku Broadband has to do with it.
In this previous article HERE, I went in-depth about how SIM swap happens in the US and how the same trend has crept into the Kenyan context.
In today’s article, I went searching for answers on how a complete stranger could know your full name, your email address, your house address in Muthaiga, your phone number, and other such details and then wipe your M-Pesa clean.
Also, how can they take down your number off the Safaricom number so quickly?
I found out a few things.
Apparently, there are three ways of doing such a fraud.
(I have to note that this is an alleged scenario not represented by facts).
The first method has to do with fake customer care calls.
Fake Zuku Customer Care Calls and M-Pesa Fraud
If you are a Zuku customer, you are likely to receive a phone call from a number that will pretend to be Zuku’s official customer care.
The number will begin with 020 and so it looks like the official line the Zuku Customer Care agents use.
Such a number could be a result of spoofing via software or it could be gotten by a hacker who simply asks Zuku to configure for him a VoIP number on his or her Triple Play subscription.
The suspicion is that these hackers could be rogue employees at Zuku or service contractors with access to and knowledge of Zuku’s network management systems.
This is because they are able to disrupt your internet connection and they will then call you pretending to be the official customer care department.
By the time they call you, you may have even complained to Zuku’s official social media pages or called their direct customer care line. Therefore, you will be inclined to think it’s the company calling you back.
The goal of this trick is to get your last M-Pesa message or amount. (They might tell you that you need to be reconnected due to the lapse of your monthly subscription).
Note that a lot of these calls happen at the end of the month when most people are renewing their internet subscriptions.
Once they get hold of your last M-Pesa transaction, they simply proceed with the SIM Swap procedure that we will talk about later on in the article.
On the same case, there is a combination of codes that hackers use to deplete your M-Pesa when pretending to be Zuku’s agents.
For example, while on the call, they might ask you for personal details and then ask you to dial certain codes on your phone, and without even opening your M-Pesa, they are able to get you to send them money.
In this fraud, you do not even have to enter your M-Pesa PIN number or such details.
It all happens with the one long code that they get you to dial (maybe with you thinking that you are resetting your internet subscription account).
Zuku’s Broadhub System and M-Pesa Scammers
In case you are smart enough to hide your M-Pesa balance when sending the fake Zuku customer care agents your proof of payment for an internet subscription, it is still possible to fall victim to another similar trap.
In this second method, the hackers use the network’s Broadhub System to find out your details.
As long as an employee or contractor has your phone number, they can get all your other details including full name, email address, house address, and more.
Remember that Zuku uses contractors to install internet for its new customers. This means there is a chance they are not aware of rogue employees or practices in their network.
With your details, a rogue employee would easily find the right target for a SIM swap fraud.
They would normally target individuals in affluent neighborhoods like Muthaiga and Runda.
(This could be the same case for contractors or rogue employees in other networks such as Safaricom).
Globally, there is an elaborate and coordinated system by hackers where they gain the personal information of victims in several steps.
I wrote about it HERE. Such a case could be said of local hackers working with roque staff and corrupted mobile loan apps.
Rogue Zuku and Safaricom Staff and Contractors in the SIM Swap Fraud
The last step for the hackers is that they will either clear your M-Pesa balance via the code manipulation described above or they will swap your SIM.
A SIM swap in this case is alleged to be done by junior employees at Safaricom’s GSM department at their switching base or Operations Support Systems.
These employees can take your number offline in a few seconds and they would then contact the hackers they are working with to proceed with the swap process.
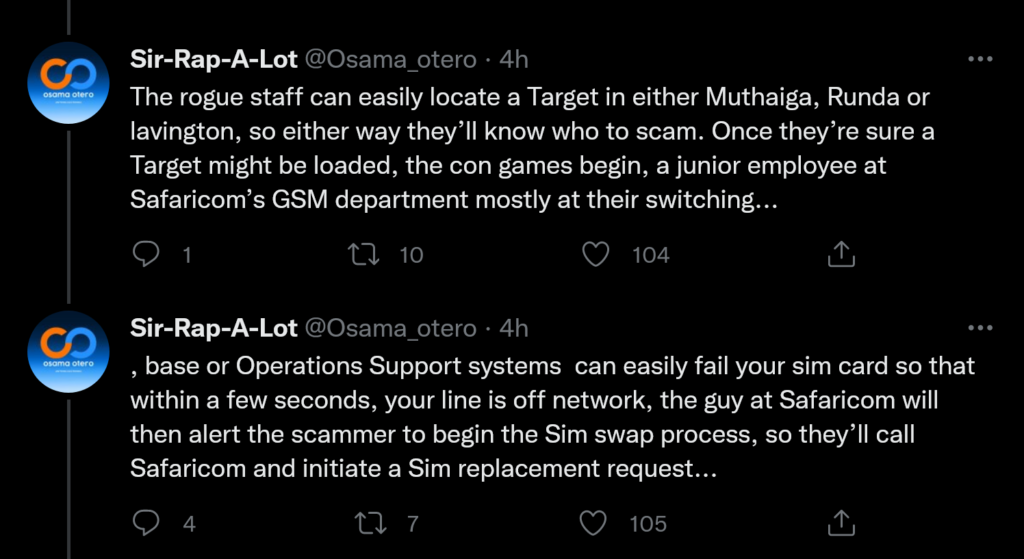
Once they are alerted, the scammers then initiate a SIM swap request.
A big problem here which also acts as the loophole is that Safaricom does not ask for the old PIN number when configuring a new line with your old number.
That’s how the scammers can just follow the normal SIM replacement procedure and get your number transferred without your consent or knowledge.
Notably, the combination of fraudsters working with the rogue staff at Zuku and Safaricom can easily result in very effective mining of personal details that would normally be restricted from the general public.
How do you protect yourself from a SIM swap fraud?
There are several steps that you can take.
I wrote this article HERE that goes into detail on what you can do.
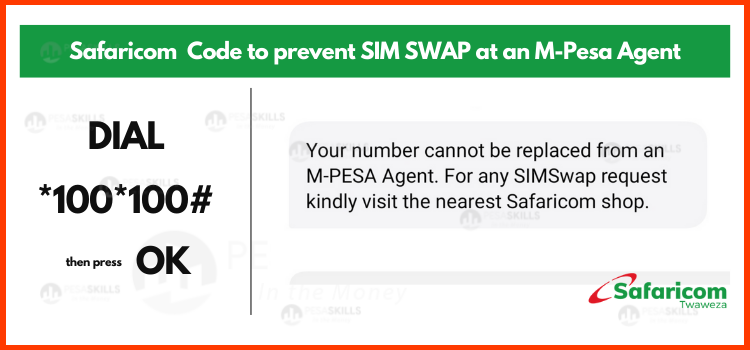
In addition to those steps I outlined in that article, a new method that has been said to work is dialing *100*100# on your Safaricom line.
This code prevents any SIM swap from happening to your number at an Agent Shop. So, the only way it can be swapped is by visiting a Safaricom Shop.
A persistent problem however is that the SIM swap is partly enabled by social engineering.
Social engineering is the process of manipulating someone to give details or do things against their better judgment.
For instance, hackers paying junior employees thousands of shillings to take your number offline is part of their social engineering.
That means that some measures that can protect you from SIM fraud are beyond your control. It would take Safaricom, Zuku, and other firms stern measures against the rogue staff and contractors in order to curb the menace.


![[Explained] – Rogue Zuku and Safaricom Staff, SIM Swap Fraud, and the Mpesa Scam](https://pesaskills.com/wp-content/uploads/2022/05/Explained-–-Rogue-Zuku-and-Safaricom-Staff-SIM-Swap-Fraud-and-the-Mpesa-Scam-750x368.png)














